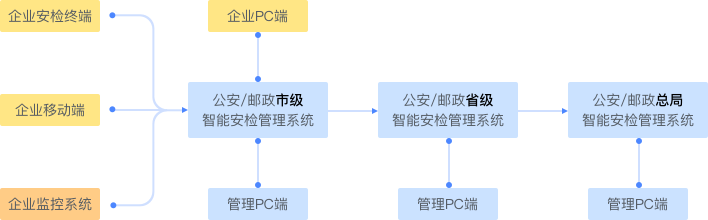
By automatically capturing images and synchronously receiving output images, centrally connecting the inspection machine of the company to the network, real-time synchronizing security data to the centralized background, including but not limited to the operation status of the security inspection machine, the working status of the security inspection machine, and the security image results and so on.
Centrally monitor the status of employment of people on each machine, operation of security inspection machine, situation of security inspection and so on of each enterprise in the network.
Centrally store and manage the security check data in the background, query and trace historical security data according to multi-dimensional, make multi-dimensionality analysis and report statist of enterprise, security equipment, security inspection results according to security data stored in the network system.
According to the requirements of the supervisory authority, the system docking supervision platform uploads the security data synchronously.
According to the algorithm of contraband’s intelligent identification, the system automatically intelligently identifies the contraband in the security image of the centralized network, and records the analysis result in the system.

The system automatically intercepts a single package image based on the security image video

System analysis of security images to automatically identify the type of contraband included

